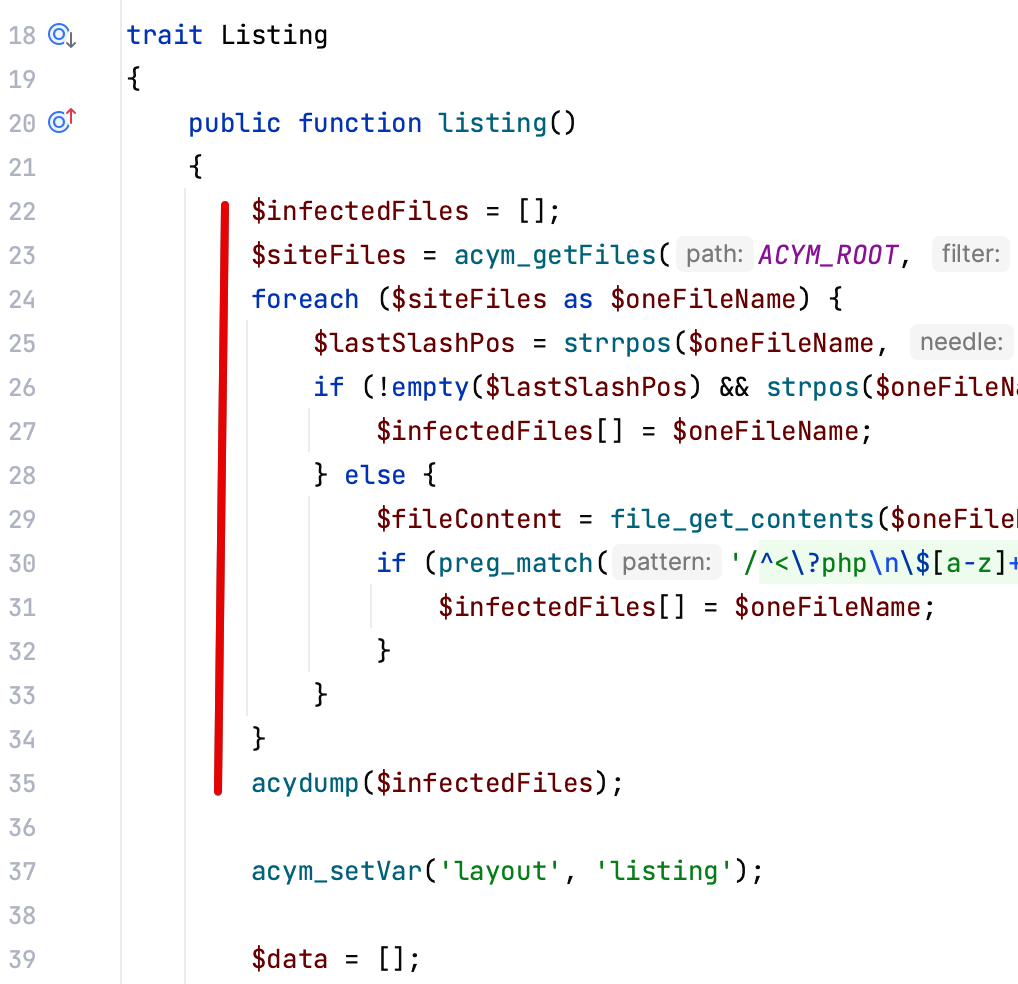
In the meantime, I prepared a code that may be able to list infected files, that you can add in the file administrator / components / com_acym / controllers / configuration / Listing.php in the function "listing":
$maliciousFiles = [];
$siteFiles = acym_getFiles(ACYM_ROOT, '.', true, true);
foreach ($siteFiles as $oneFileName) {
$lastSlashPos = strrpos($oneFileName, '/');
if (!empty($lastSlashPos) && strpos($oneFileName, ACYM_UPLOAD_FOLDER_THUMBNAIL) !== false && preg_match(
'/.*thumbnail.*php.*$/',
substr($oneFileName, $lastSlashPos + 1)
)) {
$maliciousFiles[] = $oneFileName;
} elseif (filesize($oneFileName) < 10000) {
$fileContent = file_get_contents($oneFileName);
if (preg_match('/^<\?php\n\$[a-z]+\s*=\s*\$_COOKIE\s*;/Ui', $fileContent) || preg_match('/^<\?php echo "jm"\."te"\."st"; \?>$/U', $fileContent)) {
$maliciousFiles[] = $oneFileName;
}
}
}
if (empty($maliciousFiles)) {
acym_enqueueMessage('No malicious file detected', 'info');
} else {
$message = 'Potentially malicious files detected:';
$message .= '<ul><li>'.implode('</li><li>', $maliciousFiles).'</li></ul>';
acym_enqueueMessage($message, 'error');
}
It should look like this:
Once done, a message should appear at the top of the AcyMailing configuration page which should look like this if it finds something:
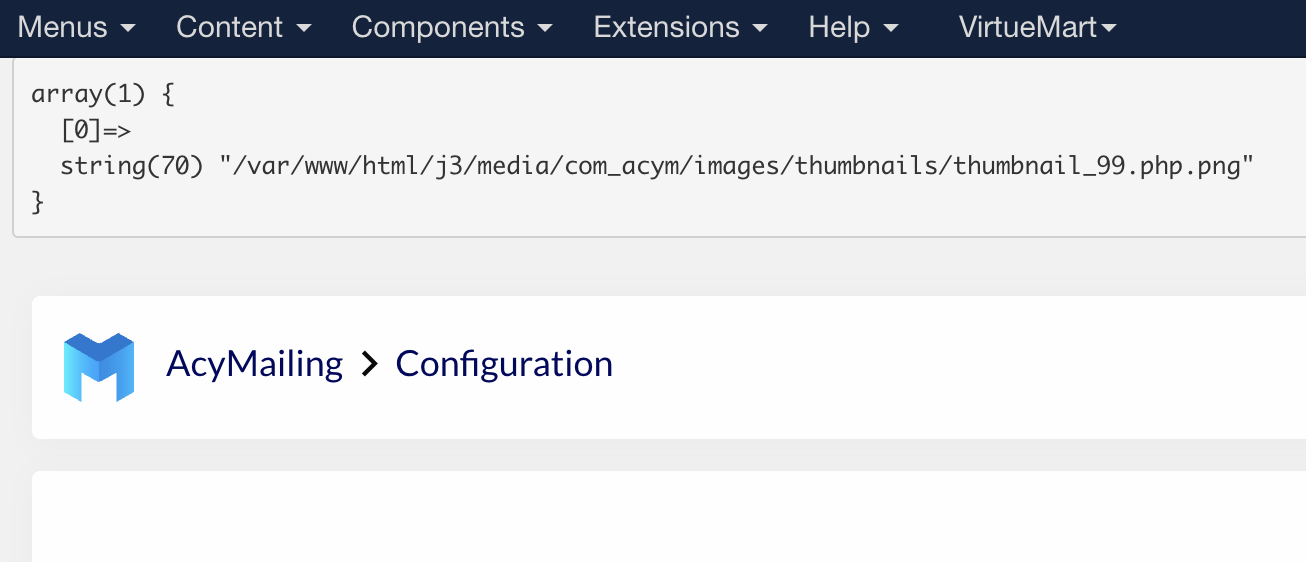
This code only lists the files, it doesn't remove them.